Ransomware Detection using ML

DOI:
https://doi.org/10.54060/a2zjournals.jase.71Keywords:
Machine Learning, Random Forest, Support Vector Machine, XGBoost, CybersecurityAbstract
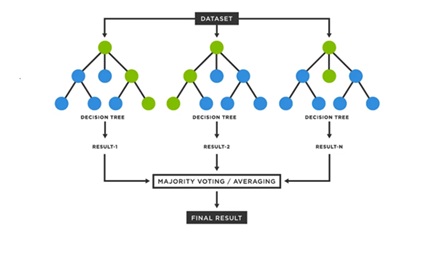
This study investigates the effectiveness of three machine learning classifi-ers—Random Forest, SVM, and XGBoost—in detecting benign files using a dataset of file features. The dataset is cleaned by removing rows with missing values and du-plicates, followed by feature scaling with StandardScaler. Correlation heatmaps and confusion matrix visualizations are used to explore data relationships and model performance. The classifiers are trained and evaluated based on accuracy, precision, recall, F1-score, and ROC-AUC. Results indicate the comparative performance of each model, highlighting their strengths and weaknesses in distinguishing between benign and non-benign files. This comprehensive approach provides insights into the most suitable classifier for this specific detection task.
Downloads
References
A. Bensalah, “ransomware detection data set.” 31-Jul-2022.
F. Noorbehbahani, F. Rasouli, and M. Saberi, “Analysis of machine learning techniques for ransomware detection,” in 2019 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), 2019.
U. Zahoora, A. Khan, M. Rajarajan, S. H. Khan, M. Asam, and T. Jamal, “Ransomware detection using deep learning based unsupervised feature extraction and a cost sensitive Pareto Ensemble classifier,” Sci. Rep., vol. 12, no. 1, pp. 1–15, 2022.
Machinelearningmastery.com [Online]. Available: https://machinelearningmastery.com/save-gradient-boosting-models-xgboost-python/. [Accessed: 20-Apr-2024].
A. Bendovschi, “Cyber-Attacks - Trends, Patterns and Security Countermeasures,” Procedia Economics and Finance, pp. 24–31, 2015.
K. Cabaj, Z. Kotulski, B. Księżopolski, and W. Mazurczyk, “Cybersecurity: trends, issues, and challenges,” EURASIP Journal on Information Security, 2018.
S. Kumar and V. Somani, “Social Media Security Risks, Cyber Threats and Risks Prevention and Mitigation Tech-niques,” International Journal of Advance Research in Computer Science and Management, vol. 4, no. 4, pp. 125–129, 2018.
Downloads
Published
How to Cite
CITATION COUNT
Issue
Section
License
Copyright (c) 2025 Ujjwal Singh, Dr P. Singh

This work is licensed under a Creative Commons Attribution 4.0 International License.



























